-

- Sopto Home
-

- Special Topic
-

- PCI-E Card Knowledge
-

- PCI Express in Wired Communications Systems
PCI-E Card Knowledge
- Info about Network Interface Card Teaming
- How to Setup a Server with Multiple Network Interface Adapters?
- How to Reconnect an Internet Network Adapter for an Acer Aspire?
- 9 Things to Do When Your Internal Network Card Stops Working
- Ethernet Standards NIC for Home Networking
- What Is a Network Interface Adapter?
- How to Configure a Network Interface Card in Linux?
- How should Configure Your NIC for ISA and TMG?
- Recommended Network Card Configuration for Forefront UAG Servers
SOPTO Special Topic
Certificate



Guarantee
Except products belongs to Bargain Shop section, all products are warranted by SOPTO only to purchasers for resale or for use in business or original equipment manufacturer, against defects in workmanship or materials under normal use (consumables, normal tear and wear excluded) for one year after date of purchase from SOPTO, unless otherwise stated...
Return Policies
Defective products will be accepted for exchange, at our discretion, within 14 days from receipt. Buyer might be requested to return the defective products to SOPTO for verification or authorized service location, as SOPTO designated, shipping costs prepaid. .....
Applications
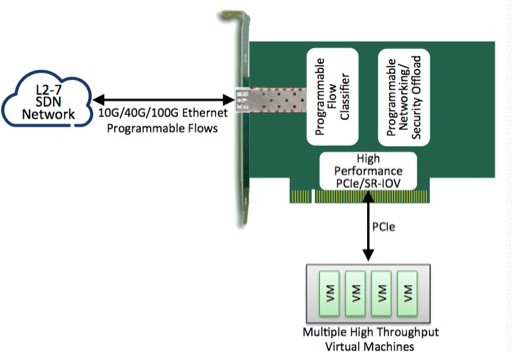
PCI-E NIC Cards provide redundant connectivity to ensure an uninterrupted network connection.
PCI-E NIC Cards are ideal for VM environments with multiple operating systems, requiring shared or dedicated NICs.
They are specially designed for desktop PC clients, servers, and workstations with few PCI Express slots available.
SOPTO Products
- Fiber Optic Transceiver Module
- High Speed Cable
- Fiber Optical Cable
- Fiber Optical Patch Cords
- Splitter CWDM DWDM
- PON Solution
- FTTH Box ODF Closure
- PCI-E Network Card
- Network Cables
- Fiber Optical Adapter
- Fiber Optical Attenuator
- Fiber Media Converter
- PDH Multiplexers
- Protocol Converter
- Digital Video Multiplexer
- Fiber Optical Tools
- Compatible
Related Products
Performance Feature
PCI-E Card Knowledge
Recommended


PCI Express in Wired Communications Systems
PCI Express, the latest generation in the PCI family of protocols, is backed by an extensive ecosystem and offers designers a high-performance, general-purpose, industry-standard interconnect at relatively low cost. Those inherent advantages are already driving its rapid adoption in the PC, server, and storage markets. Like its predecessors in the family, PCIe will inevitably find wide use in communications systems as well.
10Gigabit Ethernet Server Adapters X520 with 2 SFP+ Slots
This article will look at some of the potential applications for this popular industry-standard interconnect in the wired communications infrastructure. It will begin by examining the various tiers of the network hierarchy and how their particular data flow requirements differ.
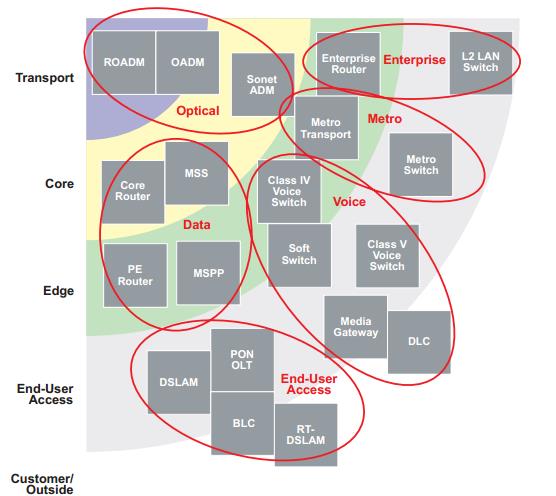
Figure 1 Communication network tiers
Transport Tier
The transport tier provides the long-haul transport of data. It is generally statically configured and cares little about the content or protocols of the data it transports. Data is tunneled through operator configured paths, with engineered fail over schemes to support high availability. These tunnels guarantee Quality of Service (QoS) by not sharing bandwidth anywhere along their route.
Core Tier
Nodes in the core tier groom traffic into predefined tunnels for transport towards its ultimate destination. These predefined tunnels are provided either by the protocol-agnostic transport tier or by dedicated point- to-point links directly between core nodes. This equipment usually prioritizes functions by referring to labels or tags added to data packets at lower network tiers. Therefore, these devices are somewhat aware of the services they carry, but due to their high aggregate data rates (hundreds of Gbps—tens of Tbps), they only have a low touch on passing data.
Edge Tier
The edge tier is generally defined as the point where a service begins and ends in a service provider’s network. Lower elements in the hierarchy aggregate or forward traffic based on very basic criteria into the edge tier where true service-aware QoS enforcement and forwarding occur. Because of the relatively expensive nature of the service-aware classification, traffic management, and forwarding functions, most network operators only deploy them on links where the relationship between peak and average loading is fairly close (on the order of 3:1). This is important because the functions must be sized to accommodate peak loads, and the disparity between peak and average loads translates into wasted capacity.
Aggregation Nodes
When a large number of small port-count access nodes exist in reasonably close proximity, it often makes economic sense to add a node between them and the edge node. These aggregation nodes smooth out the bursty but low-average-rate traffic from each access node, combining it with traffic from other access nodes. By regulating the discrepancy between peak and average loads into the edge node, these elements help the system more efficiently utilize relatively expensive edge ports. It should be noted that access nodes with large port counts inherently provide this level of averaging themselves and, therefore, connect directly to the edge nodes.
Access Tier
Defined as the network end of the “first mile,” the access tier terminates the service provider’s end of the user’s connection. In this environment, the physical placement of an access node is often dictated by the physical limitations of the protocol supported. For example, a VDSL link may be able to achieve a transfer rate to the user of 100 Mbps, but only over a distance of 300 m.
In contrast, a gigabit passive optical network (GPON) service can often reach 20 km or more from the optical line terminal to the user’s premises. Most protocols will fall between these two extremes. These physical considerations usually dictate a designer’s decisions on numbers of ports, nodal capacity, control plane capacity, and redundancy strategies. Therefore, designers typically employ a wide range of architectures in these systems.
For more information, please browse our website or contact a Sopto representative by calling 86-755-36946668, or by sending an email to info@sopto.com.